Slide 44 of 58
Notes:
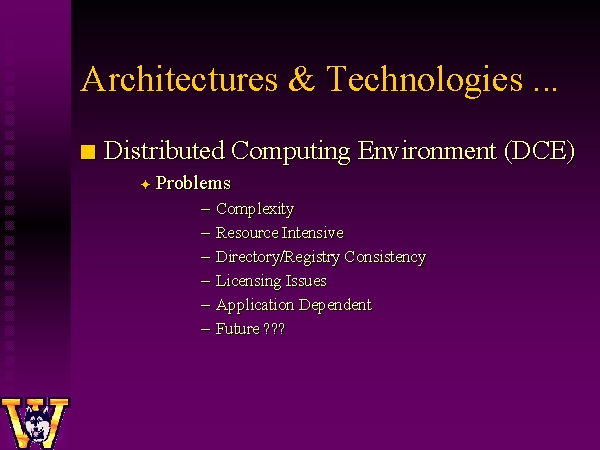
Based on our evaluation experience we found that we did not have any application requirements that might make use of vendor integrated DCE solutions. We were essentially only using the DCE K5 authentication system. We found that Directory checkpoint granularity was too coarse to ensure the synchronization that would be required for our authorization information needs. We were also surprised by the large system resources required to run our name space of 67,000 users. The security server required nearly 300MB of virtual memory for a name space of this size compared to approximately 2MB for a similar Kerberos V5 system. There were also a number of vendor implementation issues that limited interoperability. Although DCE is attractive, we found it to be more infrastructure than we required. There is also some question concerning future commitment by the vendor community in DCE. IBM recently announced a migration strategy for their DCE customers to other standards based authentication and authorization architectures.